Notes from competing in my first CTF
04/04/2023Last weekend, I competed in the National Cyber League (NCL), my first cybersecurity CTF open to students in the US. I only started my Bachelor's degree in cybersecurity a month ago but I wanted to give it a try anyway. I had a great time, learnt a lot and wanted to share some of my notes. Unfortunately, I'm not allowed to go into too much detail about the challenges and solutions but I still wanted to share some tools I used.
This CTF is broken down into 9 categories, each with multiple challenges to go through, rated from easy to hard. To avoid having people brute force the answers until they get the correct one, each time you submit an incorrect answer, your accuracy score decreases so you have to choose what you submit wisely.
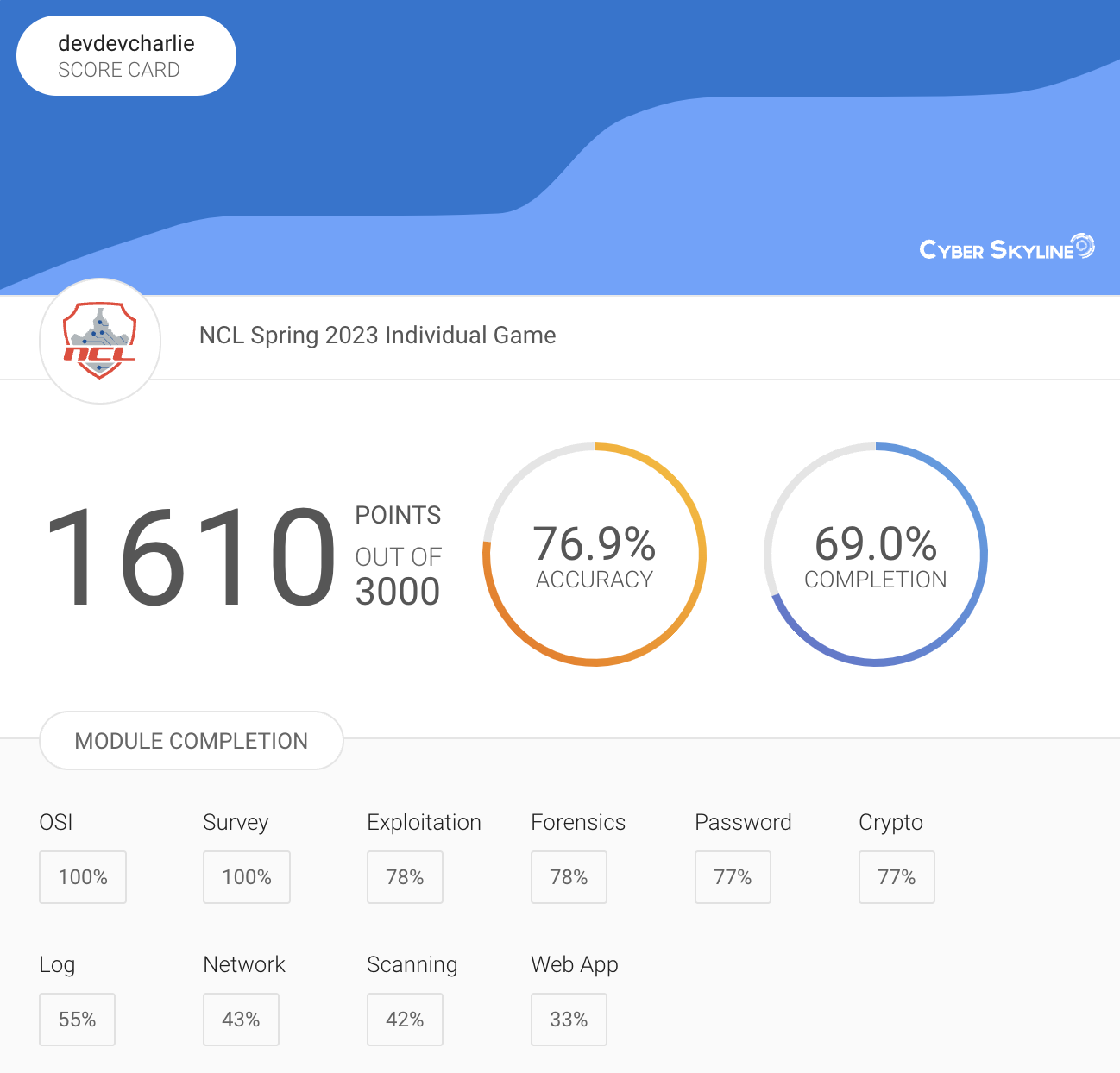
In the end, here's my score report below. I ranked in the top 6% nationally 🎉 so I'm excited to see how I do next time with more experience!
The categories include:
- Open source intelligence (OSINT)
- Cryptography
- Password Cracking
- Log analysis
- Network Traffic Analysis
- Forensics
- Scanning & Reconnaissance
- Enumeration & Exploitation
- Web application exploitation
Open-Source Intelligence (OSINT)
This section is usually related to being able to understand or find data without much context, or using notations you might not know, with very little information. For example, deciphering messages or being given a number that looks totally random and figuring out what it refers to.
Here are some of the tools I used:
- https://opennav.com/search
- https://emvlab.org/mrz/
- https://www.dcode.fr/chiffres-symboles
- Google image search
- https://ipinfo.io/
- https://www.smartconversion.com/unit_conversion/IP_Address_Converter.aspx
Cryptography
This section focuses on encrypting and decrpyting messages or files. You are often not told how they are encrypted so you have to figure out first which encryption method to use to decrypt them.
For this section, I mostly used CyberChef
For example, you could get asked to decrypt the message aGVsbG8gd29ybGQ=.
Using CyberChef, you can try to decrypt it using different methods. If you've decrypted messages before, you might recognize that it is encrypted using Base64, so it decrypts to hello world.
Some challenges also relate to finding information in files of different formats.
For challenges including files, I used commands such as file and also tools like PGP with gnupg or OpenSSL (openssl).
Password cracking
This section is pretty self-explanatory, you're given a bunch or encrypted passwords and have to figure out how to decrypt them.
For this, I downloaded wordlists such as the rockyou wordlist and used tools such as Hashcat and John the ripper.
For example, if you wanted to decode the password 5f4dcc3b5aa765d61d8327deb882cf99, you would run the following hashcat command.
hashcat -m 0 -a 0 5f4dcc3b5aa765d61d8327deb882cf99 <path to your wordlist>Web Application Exploitation
In this section, you have to find ways to attack vulnerable websites.
I mainly used the browser's developer tools, wrote some custom code and tried Burpsuite to intercept and modify requests.
Enumeration and exploitation
This section usually involves programs written in different programming languages. To solve the challenges, you might have to figure out how to run them to find the flag or answer some questions that will test your understanding of the code written.
The tools used for this section vary a lot depending on the code samples you get. You might get something in Python, JavaScript, Go, PowerShell, Assembly, etc so you have to be comfortable figuring things out.
Forensics
This section focuses on finding things in different types of files. It could involve understanding how to deal with corrupted files, being able to understand information in some config files in a format you've never worked with, or figuring out the right tool to use to extract data.
Scanning & Reconnaissance
This section is the one I am the least experienced in. It involved scanning for open ports, or finding domains connected to a server, etc.
I mainly used nmap to scan for ports and gobuster to find potential subdomains.
Log Analysis
In this section, the challenges give you different kinds of log files to analyse.
I mainly used awk to filter through the lines and extract the information I needed.
An example of command is display only the first element on each line of a log file would be
awk '{print $1}' access.logand to sort them, remove duplicates and count the number of entries, it would be something like this:
awk '{print $1}' access.log | sort | uniq | wc -lNetwork traffic analysis
In this section, you are given files with network packets and you have to analyse them to find specific information.
I mainly used Wireshark and aircrack-ng
Overall it was an intense weekend but I'm happy with how much I did and learnt. I was a bit worried about participating in a CTF before because I thought I wouldn't be able to do anything considering I have little experience in cybersecurity, but was surprised with how much I was able to solve by researching on the spot and going through the practise game a few weeks before. I'm definitely excited to learn more!